After speaking about it for months, Twitter has lastly launched its first model of encrypted DMs — however there are a couple of limitations. Presently, this characteristic is simply obtainable to verified customers (similar to Blue subscribers) or accounts related to verified organizations. Moreover, the encryption characteristic isn’t appropriate with group messages and Twitter doesn’t provide safety towards man-in-the-middle assaults.
Twitter mentioned that whereas encryption works throughout platforms, the recipient has to observe the sender to allow it. Alternatively, encryption may be enabled if a person has chatted with the sender earlier than, or accepted their DM request. If customers are eligible for an encrypted dialog, the sender will get an choice to activate encryption by way of a toggle on the brand new chat display screen.

Picture Credit: Twitter
To activate encryption for an present dialog, you may faucet on the data icon within the nook of the dialog display screen and faucet on the choice that claims “Begin an encrypted message”. Encrypted conversations will look completely different from regular dialog as Twitter locations a lock badge on the recipient’s profile image. Within the dialog itself, the corporate will present a “Messages are encrypted” banner on the high.
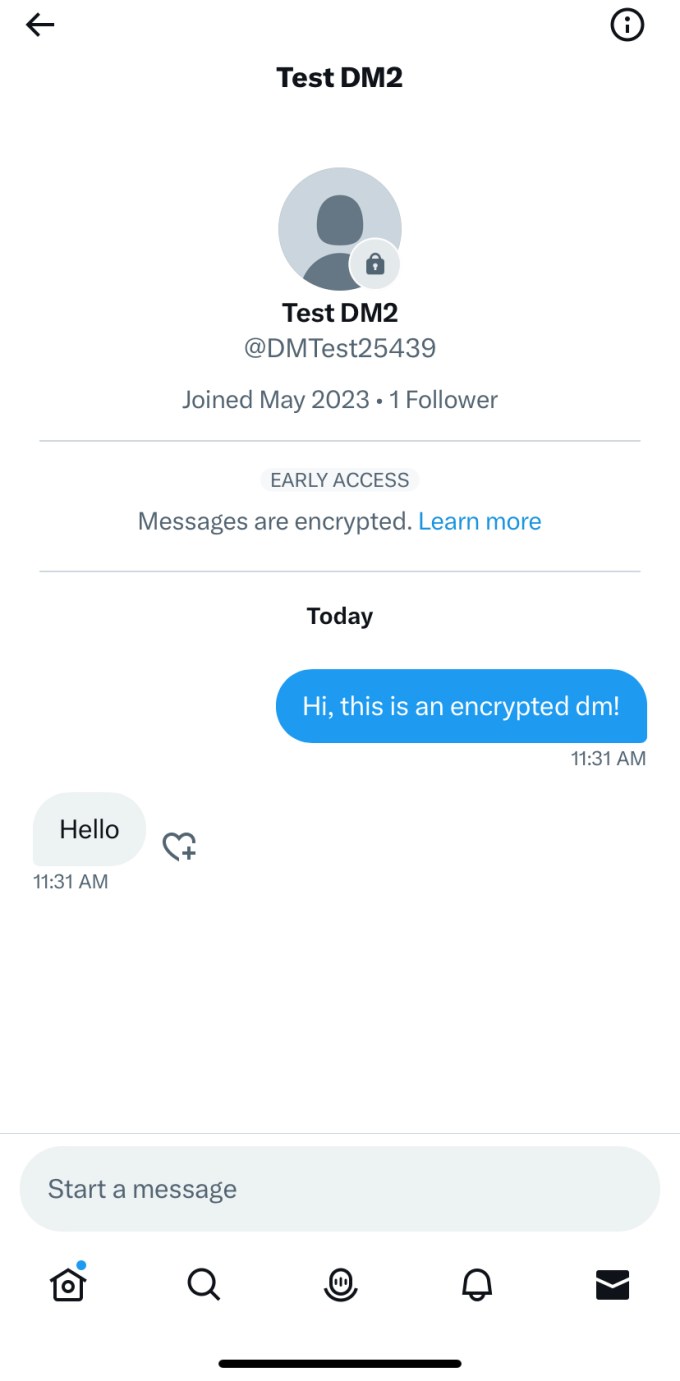
Picture Credit: Twitter
The social community makes it clear in its weblog submit that there are a number of limitations to this implementation. On the conversational degree, Twitter simply helps encryption for one-to-one messages with textual content and hyperlinks. Twitter mentioned that media is at present not supported in encrypted conversations.
Moreover, individuals can’t use a brand new machine to affix an present encrypted dialog. So that you both have to make use of the identical machine with which you initiated an encrypted dialog or begin a brand new dialog while you get a brand new machine. Customers can solely use 10 gadgets in complete to make use of the encryption characteristic, and there’s no method to deregister a tool to make room for a brand new one.
Notably, Twitter considers reinstalling the app as registering a brand new machine. Twitter doesn’t provide a key backup possibility, which signifies that all of your encrypted messages on that machine will probably be worn out in the event you sign off of the account.
However the advanced half is that Twitter doesn’t delete personal keys from the machine on logout — solely messages. Customers will be capable to fetch present conversations in the event that they log in once more from the identical machine. The corporate cautioned that individuals shouldn’t use the encryption characteristic on shared gadgets due to this limitation. This might change when Twitter begins providing a key backup possibility.
There are many doubts concerning the characteristic’s safety providing, too. It’s not clear what cryptographic normal Twitter is utilizing for this characteristic. The corporate simply mentioned it’s deploying “a mix of robust cryptographic schemes” in its weblog submit speaking concerning the encryption characteristic.
Twitter mentioned that its encryption characteristic additionally doesn’t provide ahead secrecy safety, so an attacker can entry all of a person’s previous conversations in the event that they get entry to a compromised machine. The corporate mentioned it determined to not implement this characteristic to let customers entry their unencrypted DMs on any machine.
For the time being, Twitter doesn’t provide signature checks or message verification options. So gadgets themselves can’t test the authenticity of the message and other people can’t use strategies like evaluating quantity strings to confirm encryption safety.
This makes the system weak to man-in-the-middle assaults. Meaning an attacker can learn your messages if the safety is compromised. Twitter additionally hinted that it may give this dialog as much as authorities as a part of a authorized course of because of the present design flaws.
“Because of this, if somebody — for instance, a malicious insider, or Twitter itself because of a obligatory authorized course of — have been to compromise an encrypted dialog, neither the sender nor receiver would know,” the corporate mentioned. Twitter needs so as to add signature checks and security numbers in order that these assaults or requests are now not attainable.
After taking up the corporate, Elon Musk has expressed his need to “superset Sign” with Twitter DMs. Nevertheless, with the present set of limitations, it doesn’t provide the identical degree of safety that Sign or different apps provide. Each Sign and WhatsApp provide end-to-end encryption for every kind of conversations. Moreover, Sign doesn’t log any metadata about contacts or messages.
“As Elon Musk mentioned, in the case of Direct Messages, the usual must be, if somebody places a gun to our heads, we nonetheless can’t entry your messages. We’re not fairly there but, however we’re engaged on it,” the corporate mentioned.
