
Menace actors are selling a brand new ‘Exfiltrator-22’ post-exploitation framework designed to unfold ransomware in company networks whereas evading detection.
Menace analysts at CYFIRMA declare that this new framework was created by former Lockbit 3.0 associates who’re specialists in anti-analysis and protection evasion, providing a sturdy resolution in trade for a subscription charge.
The costs for Exfiltrator-22 vary between $1,000 per thirty days and $5,000 for lifetime entry, providing steady updates and help.
Patrons of the framework are given an admin panel hosted on a bulletproof VPS (digital personal server) from the place they will management the framework’s malware and challenge instructions to compromised programs.
The primary model of the Exfiltrator-22 (EX-22) appeared within the wild on November 27, 2022, and roughly ten days later, its authors arrange a Telegram channel to promote the framework to different cybercriminals.
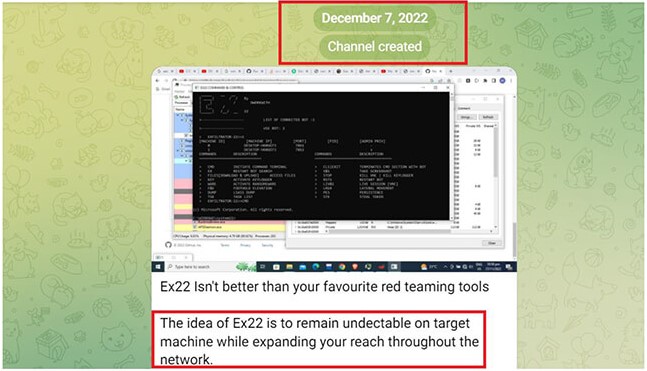
By the tip of the 12 months, the menace actors introduced new options that helped conceal visitors on compromised units, indicating that the framework was beneath lively improvement.
In January 2023, EX-22 was deemed 87% prepared by its authors, and subscription costs have been introduced, inviting customers to buy entry to the software.
On February 10, 2023, the menace actors posted two demonstration movies on YouTube to showcase EX-22’s lateral motion and ransomware-spreading capabilities.
Exfiltrator-22 options
EX-22 contains options generally present in different post-exploitation toolkits but in addition further options geared in direction of deploying ransomware and information theft.
The spotlight options included within the framework are:
- Set up a reverse shell with elevated privileges.
- Add recordsdata to the breached system or obtain recordsdata from the host to the C2.
- Activate a keylogger to seize keyboard enter.
- Activate a ransomware module to encrypt recordsdata on the contaminated system.
- Seize a screenshot from the sufferer’s pc.
- Begin a reside VNC (Digital Community Computing) session for real-time entry on the compromised system.
- Acquire greater privileges on the contaminated system.
- Set up persistence between system reboots.
- Activate a worm module that spreads the malware to different units on the identical community or the general public web.
- Extract information (passwords and tokens) from the LSAAS (Native Safety Authority Subsystem Service).
- Generate cryptographic hashes of recordsdata on the host to assist intently monitor file places and content material change occasions.
- Fetch the checklist of operating processes on the contaminated system.
- Extract authentication tokens from the breached system.
The above instructions are despatched to compromised units by way of the Home windows ‘EX22 Command & Management’ console program.
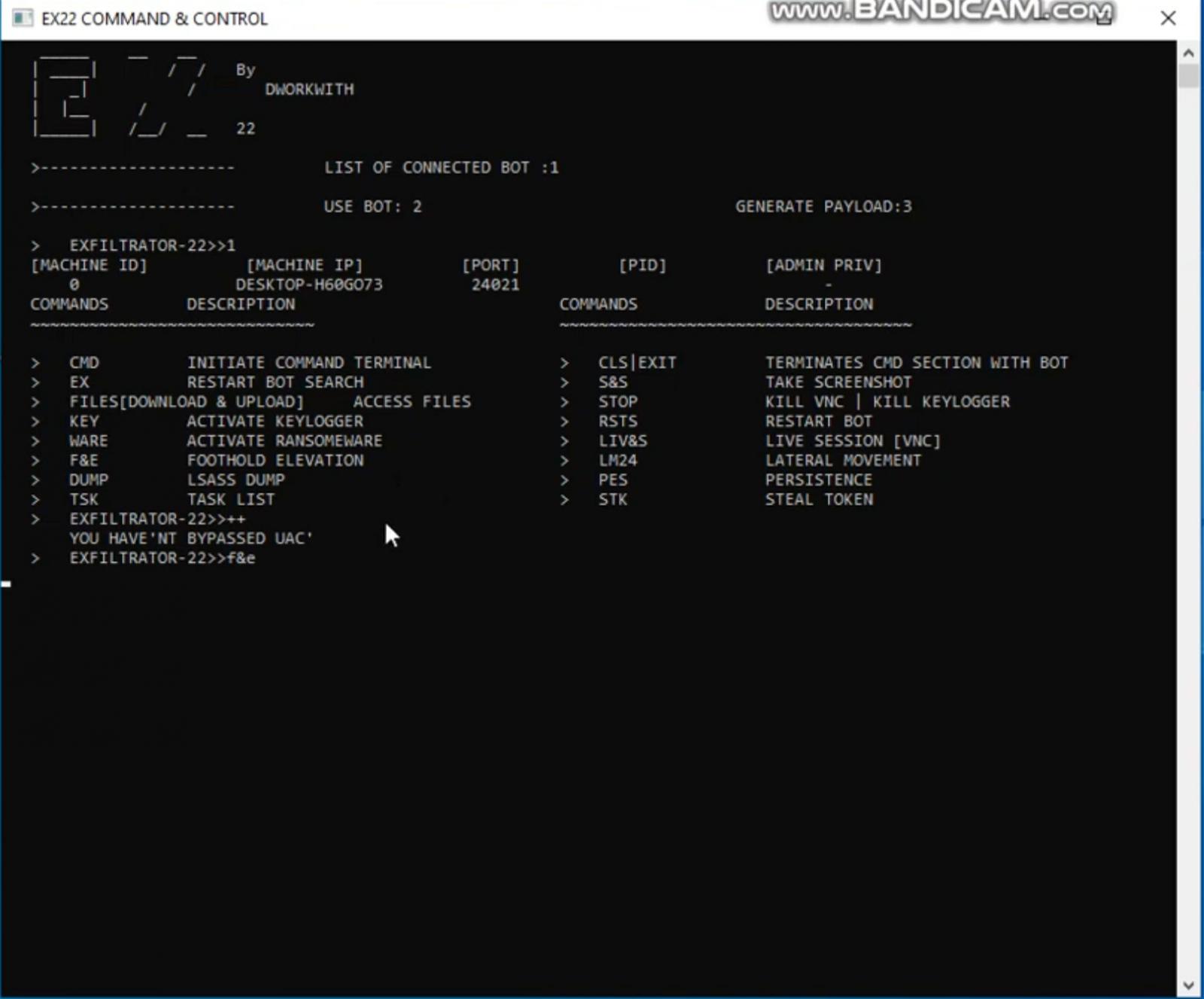
These instructions’ outputs are then returned to the command and management server and displayed instantly within the console software, as proven under.
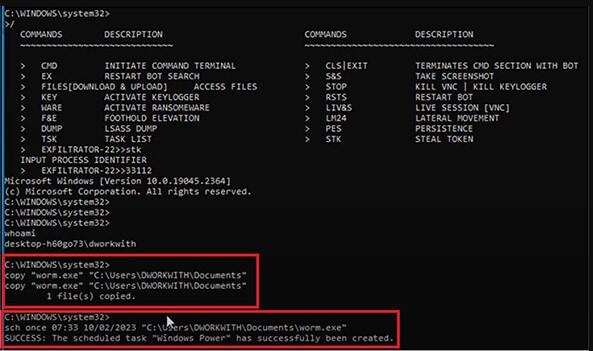
By way of the service’s internet panel, cybercriminals can even set scheduled duties, replace brokers to a brand new model, change a marketing campaign’s configuration, or create new campaigns.
Linked to LockBit ransomware members
The CYFIRMA workforce has discovered proof that LockBit 3.0 associates or members of the ransomware operation’s improvement workforce are behind EX-22.
First, they observed that the framework makes use of the identical “area fronting” approach related to the LockBit and the TOR obfuscation plugin Meek, which helps cover malicious visitors inside respectable HTTPS connections to respected platforms.
Upon additional investigation, CYFIRMA has discovered that EX-22 additionally makes use of the identical C2 infrastructure beforehand uncovered in a LockBit 3.0 pattern.
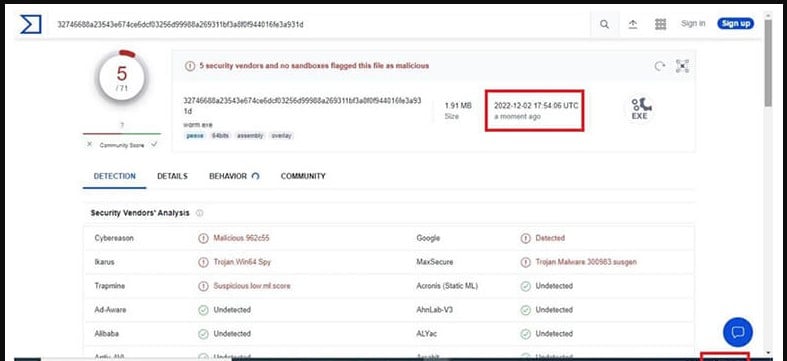
Sadly, Exfiltrator-22 seems to have been created by educated malware authors who possess the talents to develop an evasive framework.
Therefore, it’s anticipated to generate a lot curiosity within the cybercrime group regardless of its excessive worth, naturally leading to additional code improvement and have enhancements.
