A beforehand undetected superior persistent menace (APT) actor dubbed Purple Stinger has been linked to assaults concentrating on Japanese Europe since 2020.
“Army, transportation, and significant infrastructure have been a number of the entities being focused, in addition to some concerned within the September East Ukraine referendums,” Malwarebytes disclosed in a report printed at this time.
“Relying on the marketing campaign, attackers managed to exfiltrate snapshots, USB drives, keyboard strokes, and microphone recordings.”
Purple Stinger overlaps with a menace cluster Kaspersky revealed underneath the title Unhealthy Magic final month as having focused authorities, agriculture, and transportation organizations positioned in Donetsk, Lugansk, and Crimea final 12 months.
Whereas there have been indications that the APT group could have been lively since no less than September 2021, the newest findings from Malwarebytes push the group’s origins again by almost a 12 months, with the primary operation happening in December 2020.
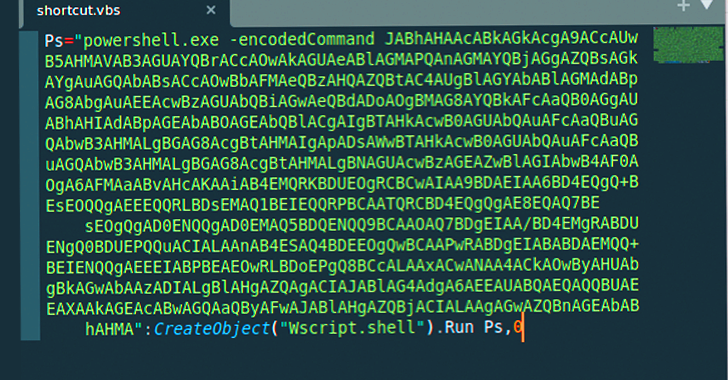
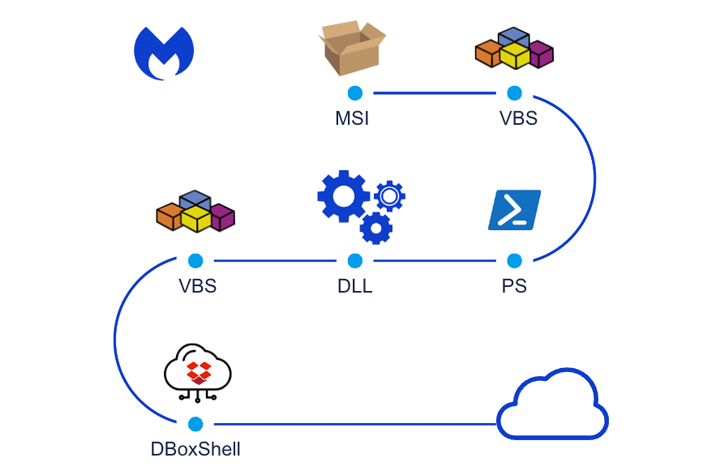
The assault chain, on the time, is alleged to have leveraged malicious installer recordsdata to drop the DBoxShell (aka PowerMagic) implant on compromised methods. The MSI file, for its half, is downloaded by the use of a Home windows shortcut file contained inside a ZIP archive.
Subsequent waves detected in April and September 2021 have been noticed to leverage comparable assault chains, albeit with minor variations within the MSI file names.
A fourth set of assaults coincided with the onset of Russia’s navy invasion of Ukraine in February 2022. The final recognized exercise related to Purple Stinger befell in September 2022, as documented by Kaspersky.
“DBoxShell is malware that makes use of cloud storage companies as a command-and-control (C&C) mechanism,” safety researchers Roberto Santos and Hossein Jazi mentioned.
“This stage serves as an entry level for the attackers, enabling them to evaluate whether or not the targets are fascinating or not, which means that on this part they’ll use totally different instruments.”
The fifth operation can be notable for delivering an alternative choice to DBoxShell known as GraphShell, which is so named for its use of the Microsoft Graph API for C&C functions.
The preliminary an infection part is adopted by the menace actor deploying further artifacts like ngrok, rsockstun (a reverse tunneling utility), and a binary to exfiltrate sufferer knowledge to an actor-controlled Dropbox account.
The precise scale of the infections are unclear, though proof factors to 2 victims positioned in central Ukraine – a navy goal and an officer working in important infrastructure – who have been compromised as a part of the February 2022 assaults.
Study to Cease Ransomware with Actual-Time Safety
Be part of our webinar and learn to cease ransomware assaults of their tracks with real-time MFA and repair account safety.
In each situations, the menace actors exfiltrated screenshots, microphone recordings, and workplace paperwork after a interval of reconnaissance. One of many victims additionally had their keystrokes logged and uploaded.
The September 2022 intrusion set, however, is notable for the truth that it mainly singled out Russia-aligned areas, together with officers and people concerned in elections. One of many surveillance targets had knowledge from their USB drives exfiltrated.
Malwarebytes mentioned it additionally recognized a library within the Ukrainian metropolis of Vinnytsia that was contaminated as a part of the identical marketing campaign, making it the one Ukraine-related entity to be focused. The motivations are presently unknown.
Whereas the origins of the menace group are a thriller, it has emerged that the menace actors managed to contaminate their very own Home windows 10 machines in some unspecified time in the future in December 2022, both unintentionally or for testing functions (given the title TstUser), providing an perception into their modus operandi.
Two issues stand out: The selection of English because the default language and the usage of Fahrenheit temperature scale to show the climate, seemingly suggesting the involvement of native English audio system.
“On this case, attributing the assault to a selected nation is just not a simple job,” the researchers mentioned. “Any of the concerned nations or aligned teams could possibly be accountable, as some victims have been aligned with Russia, and others have been aligned with Ukraine.”
“What is obvious is that the principal motive of the assault was surveillance and knowledge gathering. The attackers used totally different layers of safety, had an in depth toolset for his or her victims, and the assault was clearly focused at particular entities.”