
Ongoing assaults are concentrating on an Unauthenticated Saved Cross-Website Scripting (XSS) vulnerability in a WordPress cookie consent plugin named Lovely Cookie Consent Banner with greater than 40,000 lively installs.
In XSS assaults, risk actors inject malicious JavaScript scripts into weak web sites that can execute inside the guests’ internet browsers.
The impression can embrace unauthorized entry to delicate data, session hijacking, malware infections by way of redirects to malicious web sites, or an entire compromise of the goal’s system.
WordPress safety firm Defiant, which noticed the assaults, says the vulnerability in query additionally permits unauthenticated attackers to create rogue admin accounts on WordPress web sites operating unpatched plugin variations (as much as and together with 2.10.1).
The safety flaw exploited on this marketing campaign was patched in January with the discharge of model 2.10.2.
“In accordance with our data, the vulnerability has been actively attacked since February 5, 2023, however that is the most important assault towards it that we now have seen,” risk analyst Ram Gall mentioned.
“We’ve blocked practically 3 million assaults towards greater than 1.5 million websites, from practically 14,000 IP addresses since Could 23, 2023, and assaults are ongoing.”
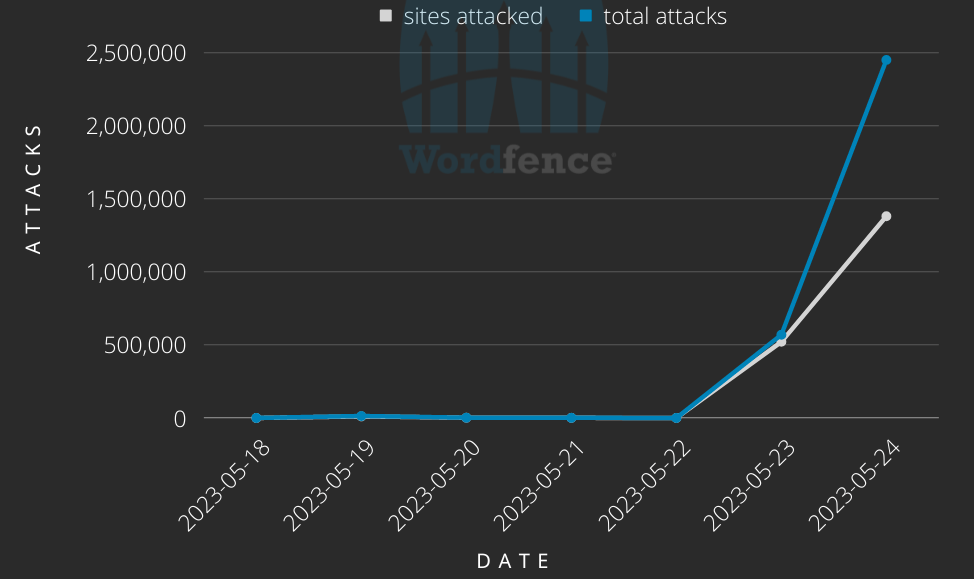
Regardless of the large-scale nature of this ongoing assault marketing campaign, Gall says the risk actor makes use of a misconfigured exploit that may seemingly not deploy a payload even when concentrating on a WordPress web site operating a weak plugin model.
Even so, admins or house owners of internet sites utilizing the Lovely Cookie Consent Banner plugin are suggested to replace it to the most recent model as a result of even a failed assault might corrupt the plugin’s configuration saved within the nsc_bar_bannersettings_json choice.
The plugin’s patched variations have additionally been up to date to restore itself within the occasion that the web site was focused in these assaults.
Whereas the present wave of assaults won’t be capable to inject web sites with a malicious payload, the risk actor behind this marketing campaign might handle this problem at any time and doubtlessly infect any websites that stay uncovered.
Final week, risk actors additionally began probing the web for WordPress web sites operating weak variations of the Important Addons for Elementor and WordPress Superior Customized Fields plugins.
The campaigns began after the discharge of proof-of-concept (PoC) exploits, permitting unauthenticated attackers to hijack web sites after resetting admin passwords and gaining privileged entry, respectively.
