
Industrial cybersecurity firm Dragos at the moment disclosed what it describes as a “cybersecurity occasion” after a identified cybercrime gang tried to breach its defenses and infiltrate the inner community to encrypt gadgets.
Whereas Dragos states that the risk actors didn’t breach its community or cybersecurity platform, they received entry to the corporate’s SharePoint cloud service and contract administration system.
“On Could 8, 2023, a identified cybercriminal group tried and failed at an extortion scheme towards Dragos. No Dragos programs have been breached, together with something associated to the Dragos Platform,” the corporate mentioned.
“The felony group gained entry by compromising the non-public e mail deal with of a brand new gross sales worker previous to their begin date, and subsequently used their private info to impersonate the Dragos worker and achieve preliminary steps within the worker onboarding course of.”
After breaching Dragos’ SharePoint cloud platform, the attackers downloaded “normal use information” and accessed 25 intel experiences that have been often solely out there to prospects.
Through the 16 hours they’d entry to the worker’s account, the risk actors did not additionally entry a number of Dragos programs—together with its messaging, IT helpdesk, monetary, request for proposal (RFP), worker recognition, and advertising programs—on account of role-based entry management (RBAC) guidelines.
After failing to breach the corporate’s inner community, they despatched an extortion e mail to Dragos executives 11 hours into the assault. The message was learn 5 hours later as a result of it was despatched outdoors enterprise hours.
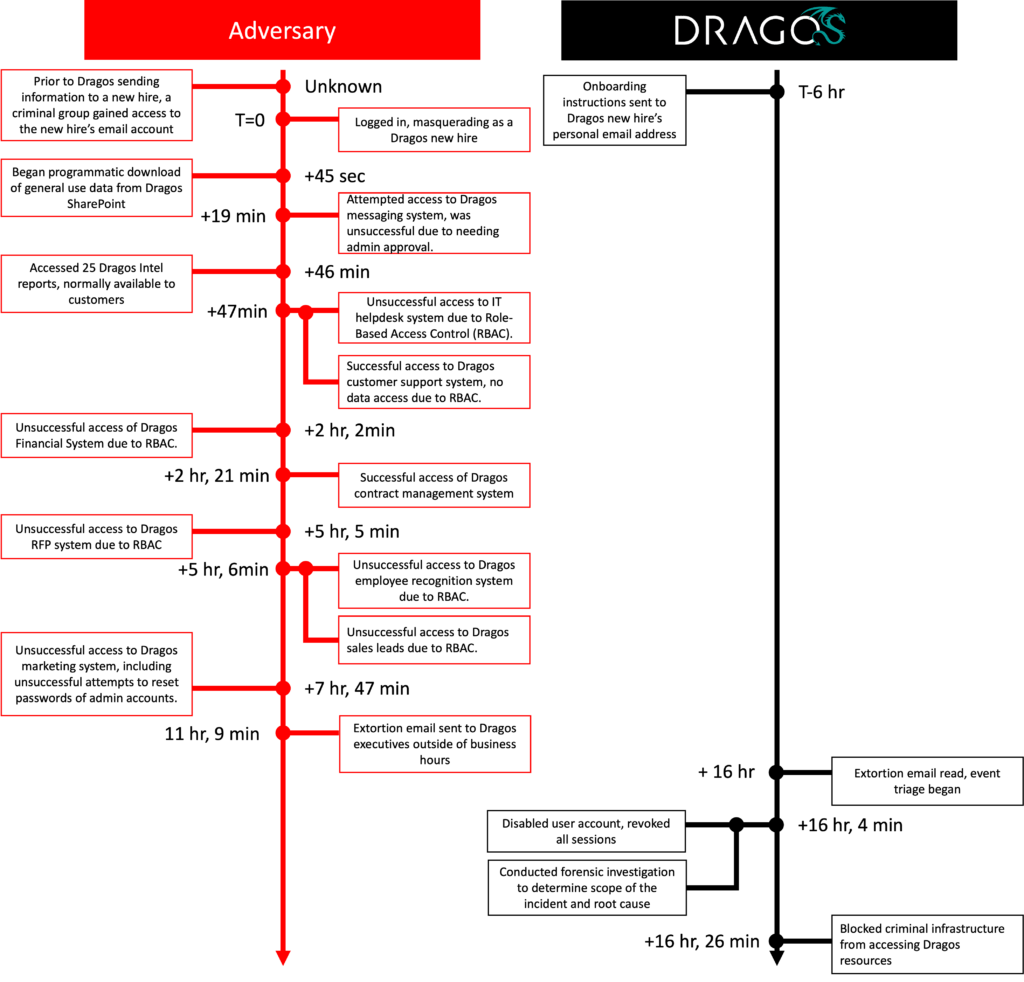
5 minutes after studying the extortion message, Dragos disabled the compromised certain account, revoked all lively periods, and blocked the cybercriminals’ infrastructure from accessing firm sources.
“We’re assured that our layered safety controls prevented the risk actor from carrying out what we consider to be their major goal of launching ransomware,” Dragos mentioned.
“They have been additionally prevented from carrying out lateral motion, escalating privileges, establishing persistent entry, or making any adjustments to the infrastructure.”
The cybercrime group additionally tried to extort the corporate by threatening to publicly disclose the incident in messages despatched through public contacts and private emails belonging to Dragos executives, senior staff, and their members of the family.
“Whereas the exterior incident response agency and Dragos analysts really feel the occasion is contained, that is an ongoing investigation. The information that was misplaced and more likely to be made public as a result of we selected to not pay the extortion is regrettable,” Dragos concluded.
One of many IP addresses listed within the IOCs (144.202.42[.]216) was beforehand noticed internet hosting the SystemBC malware, generally utilized by ransomware gangs for distant entry to compromised programs.
CTI Researcher Will Thomas from Equinix advised BleepingComputer that SystemBC has been utilized by quite a few ransomware gangs, together with Conti, ViceSociety, BlackCat, Quantum, Zeppelin, and Play, making it arduous to pinpoint what risk actor is behind the assault.
Thomas mentioned that the IP deal with has additionally been seen utilized in current BlackBasta ransomware assaults, probably narrowing down the suspects.
A Dragos spokesperson mentioned they’d reply later when BleepingComputer reached out for extra particulars on the cybercrime group behind this incident.
